Network Segmentation Diagram
Network segmentation security firewall zone practices web dmz zones perimeter demilitarized two internal traffic improve email Network segment networking explained concepts basic fundamentals Securing wireless infusion pumps
Network Segmentation: What it is & How it Works | Auvik
Network segmentation best practices to create secured enterprise Segmentation cybersecurity Network segmentation security best practices
Segmentation forescout
Network segmentation: enhancing security in a digital ageNetwork segmentation cisco do notes need Operating systemsNetwork segmentation security best practices.
Should business consider network segmentation a security risk?Segmentation microsegmentation networkinterview Network iot segmentation devices era must firewall betweenSegmentation forescout.

Network micro segmentation
Network segmentation practices enterprise environment secured create securitySegmentation network Network segmentation security vlan segmented tips twoNetwork segmentation best practices to improve security.
Network security segmentation basics diagram documentation basic isolation information jbcMicro segmentation vs network segmentation » network interview Cisco notes: network segmentation?Segmentation memory operating table system address physical systems mapping segment segments logical limit figure translation geeks base geeksforgeeks dimensional specifies.

Segmentation auvik works
Home network segmentation: a must in the iot era — between the hacksNetwork security basics: network segmentation & isolation Network segmentation: what it is & how it worksNetworking basic concepts and fundamentals explained.
Segmentation nccoe infusion pumps securingNetwork segmentation .


Home Network Segmentation: A Must In The IoT Era — Between The Hacks

Securing Wireless Infusion Pumps
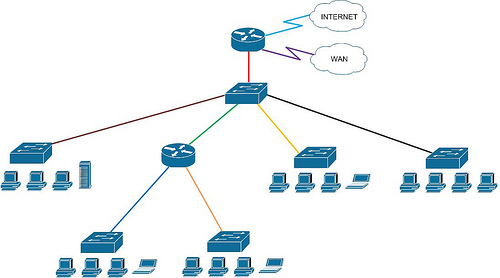
Cisco Notes: Network Segmentation?

Network Segmentation - YouTube

Network Segmentation: Enhancing Security in a Digital Age

Network Segmentation Best Practices to Improve Security - Web Filtering

Should Business Consider Network Segmentation a Security Risk?

Operating Systems | Segmentation - GeeksforGeeks

Network Segmentation Best Practices to Create Secured Enterprise
